Cross-Site Request Forgery (CSRF) is a type of web security vulnerability where an attacker tricks a user into unknowingly making an unwanted and potentially harmful request to a web application on which the user is authenticated. This occurs because the web application does not properly validate the origin of the request, allowing the attacker to perform actions on behalf of the user without their consent.
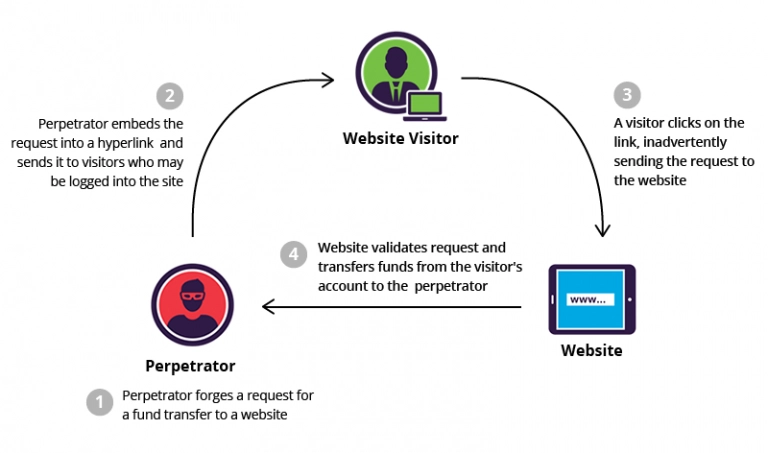
Here's an example to help you understand CSRF:
Suppose there's an online banking application that allows users to transfer money to other accounts by submitting a POST request to the URL: https://bank.example.com/transfer.
User Authentication:
- Alice logs into her online banking account at
https://bank.example.comand gets authenticated. She receives a session cookie that her browser will include in subsequent requests to prove her identity.
- Alice logs into her online banking account at
Attacker's Trap:
The attacker, Eve, creates a malicious website or sends Alice a link to a webpage she controls. This webpage contains a hidden form that targets the bank's transfer URL and includes fields for transferring money:
<form action="https://bank.example.com/transfer" method="POST"> <input type="hidden" name="toAccount" value="Eve's Account"> <input type="hidden" name="amount" value="10000"> <!-- More fields might be needed, like Alice's session cookie --> <input type="submit" value="Click to Win a Prize"> </form>
Alice's Interaction:
- Alice, who is still authenticated in her banking session, visits Eve's malicious webpage. Unbeknownst to her, the hidden form is automatically submitted due to the presence of the
<input type="submit">element.
- Alice, who is still authenticated in her banking session, visits Eve's malicious webpage. Unbeknownst to her, the hidden form is automatically submitted due to the presence of the
Unwanted Action Triggered:
- Alice's browser sends a POST request to
https://bank.example.com/transferwith the data to transfer $10,000 to Eve's account. The request includes Alice's session cookie, so the bank's server believes this request is legitimate and coming from Alice herself.
- Alice's browser sends a POST request to
Impact:
- The bank's server processes the request, deducting $10,000 from Alice's account and crediting it to Eve's account. Since the request came from Alice's browser, the server does not distinguish between legitimate and malicious actions.
In this scenario, the CSRF attack was successful because the bank's application did not implement proper measures to prevent unauthorized requests based on the origin of the request. To prevent CSRF attacks, web applications can use techniques like including anti-CSRF tokens in forms or requiring additional user confirmation for sensitive actions.
In general, protecting against CSRF involves validating the source of incoming requests, ensuring that actions require explicit user consent, and employing security mechanisms to prevent unauthorized requests.
Protecting against Cross-Site Request Forgery (CSRF) in Rails
In Ruby on Rails, protecting against Cross-Site Request Forgery (CSRF) attacks is built into the framework by default. Rails provides a set of mechanisms to prevent CSRF attacks, and developers need to follow best practices to ensure their applications are secure. Here's how you can avoid CSRF attacks in a Rails application:
CSRF Token: Rails automatically generates a unique CSRF token for each user session and includes it in forms and AJAX requests. This token is required for all non-GET requests and is validated by the server to ensure that the request originated from the same application and the same user. To use the CSRF token in forms, you can use the
csrf_meta_tagshelper and thecsrf_tokenhelper. In forms, include the token like this:<%= csrf_meta_tags %> <%= form_with(model: @user) do |form| %> # Form fields <%= form.submit %> <% end %>protect_from_forgeryMethod: In your application'sApplicationController, you should have theprotect_from_forgerymethod called. This method adds the CSRF protection filter to all controllers, ensuring that the CSRF token is validated for non-GET requests. This is the default behavior for new Rails applications.class ApplicationController < ActionController::Base protect_from_forgery with: :exception # ... endAPIs and CSRF: If your Rails application serves an API, you might want to disable CSRF protection for API requests. In such cases, you can use different strategies to protect your APIs, like using token-based authentication or implementing your own authorization mechanisms.
AJAX Requests: When making AJAX requests, ensure that you include the CSRF token in the request headers. Rails provides a convenient way to do this using the
metatag generated by thecsrf_meta_tagshelper. You can extract the token from the meta tag and set it as a header in your AJAX requests.var csrfToken = document.querySelector('meta[name="csrf-token"]').getAttribute('content'); $.ajax({ // ... headers: { 'X-CSRF-Token': csrfToken } });
By following these practices, your Ruby on Rails application will be well-protected against CSRF attacks. However, always stay updated with the latest security practices and Rails updates to ensure the continued security of your application.
Protecting against Cross-Site Request Forgery (CSRF) in Django
In Django, protecting against Cross-Site Request Forgery (CSRF) attacks is also a built-in feature. The framework provides strong protection against CSRF attacks by default, and you can take advantage of these features to secure your Django application. Here's how to avoid CSRF attacks in a Django application:
CSRF Middleware: Django includes a middleware called
CsrfViewMiddlewarethat handles CSRF protection. This middleware requires a CSRF token for all non-safe (non-GET) requests. The token is typically included in forms and AJAX requests to verify the origin of the request.To enable this middleware, ensure that it's listed in the
MIDDLEWAREsetting in yoursettings.pyfile. It's usually enabled by default in new Django projects.CSRF Token in Forms: In Django templates, you can use the
{% csrf_token %}template tag to include the CSRF token in your HTML forms. This tag generates an input field with the CSRF token value.<form method="post"> {% csrf_token %} <!-- Form fields --> <button type="submit">Submit</button> </form>AJAX Requests: When making AJAX requests, you need to include the CSRF token in the request headers. You can extract the CSRF token value from the cookie and include it as a header in your AJAX requests. The cookie name is usually
csrftoken.var csrfToken = Cookies.get('csrftoken'); // Use a cookie library like js-cookie $.ajax({ // ... headers: { "X-CSRFToken": csrfToken } });@csrf_protectDecorator: In cases where you need more control over CSRF protection, you can use the@csrf_protectdecorator on specific views. This allows you to apply CSRF protection only to selected views, overriding the default behavior.from django.views.decorators.csrf import csrf_protect @csrf_protect def my_view(request): # ...Exempting Views: If you need to exempt certain views from CSRF protection (for example, views intended for external API access), you can use the
@csrf_exemptdecorator.from django.views.decorators.csrf import csrf_exempt @csrf_exempt def api_view(request): # ...
Django's built-in CSRF protection mechanisms should be sufficient to safeguard your application against CSRF attacks. However, make sure you stay up-to-date with the latest Django updates and security best practices to ensure the ongoing security of your application.

